- Incorta Community
- Knowledge
- Administration Knowledgebase
- Integrating with Active Directory
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
03-14-2022
03:16 PM
- edited on
10-04-2022
08:04 AM
by
KailaT
![]()
Introduction
Many companies use Microsoft Active Directory to manage users and access to corporate networks. For Incorta, it is often beneficial for the customer to manage users that will have access to Incorta by assigning them to one or more user groups within Active Directory. It is then possible, using LDAP synchronization with Active Directory, to pull those users and groups maintained in Active Directory into Incorta. It is also possible, using LDAP, to use Active Directory as a Secure Sign-on (SSO) method where the user will be Authenticated to Active Directory when they sign into Incorta. Both of these topics will be discussed below.
What you should know before reading this article
We recommend that you be familiar with these Incorta concepts before exploring this topic further.
- Your company's utilization of Active Directory: Group and User creation & management
- Incorta Docs: User and Group Security
- Incorta Docs: Configuration of LDAP
Applies to
These concepts apply to all releases of Incorta.
Let's Go
Synchronizing Users and Groups with Active Directory via LDAP
In order to synchronize your company's Active Directory with Incorta via LDAP, you will need to:
- Configure the ldap-config.properties file found in the <incorta-install-path>/IncortaAnalytics/IncortaNode/bin directory
- Update the sync_directory_with_ldap.sh script file found in the same directory as the properties file with information needed on how to log in to your Incorta application
- If you want to synchronize with your Active Directory on a regular basis, you will have to use cron or some other scheduling application to run the script file above regularly (daily, weekly, etc.)
Configuring the LDAP properties file
You will need to gather the following information from your IT group to update specific lines in the properties file including
- ldap.base.provider.url: Your LDAP access URL and Port Number
- ldap.base.dn: Your company Domain information such as "DC=<your company>,DC=com"
- ldap.user.dn & ldap.user.dn.password: User ID and Password required for the script to login to the URL provided above
- ldap.user.search.filter: contains a specific syntax for finding "members of" specific Groups within your Active Directory that you have created. The following example shows a search from 2 groups "=(&(objectCategory=person)(mail=*)(|(memberOf=CN=yourcompany-incorta-ro,OU=Incorta,OU=Security Groups,DC=yourcompany,DC=com)(memberOf=CN=yourcompany-incorta-cc,OU=Incorta,OU=Security Groups,DC=yourcompany,DC=com)))"
- ldap.group.search.filter: The search filter for finding Groups. The syntax for this filter allows using a wildcard, so it is a best practice to name all of your Incorta Groups in Active Directory as "yourcompany-incorta-" and the resulting search would be coded as "=(&(objectClass=group)(name=yourcompany-incorta-*))
- user.type: used to tell Incorta what type of user to create with the synchronization:
- Internal: Incorta authentication will be controlled by ID and Password managed by Incorta
- LDAP: Incorta authentication will be controlled by LDAP (see the section below on this topic)
- SSO: Incorta authentication will be controlled by another SSO Vendor Software
Note:
- Every group you want to synchronize with Incorta must be in this search string and must be formatted as shown in the example based on your domain and OU node setup in Active Directory. Repeating the string: (memberOf=CN=<group-name>,OU=<OU level n>,OU=<OU level 2>,OU=<OU level 1>,DC=yourcompany,DC=com)
- The above example shows that there are 2 domain nodes (OUs) underneath yourcompany.com where Groups are created, and then a node for the Incorta Groups. Essentially, this syntax needs to be used to create the path to where to find the groups to search for the people. Your Active Directory Admin will tell you how this structure needs to be coded to find the Groups.
Configuring the synchronization script
The script file will use the properties file created above to do the following:
- login to your LDAP server
- Get 3 lists: User, Groups, and Users Mapped to Groups
- Login to Incorta
- Insert & Update Users and Groups with the information pulled from Active directory. Note: User deletes are NOT supported as part of the LDAP synchronization. This is purposeful, because once a user is created, they may own content (dashboards, schemas, etc.), and when a user is deleted, so is all of the content associated with that user. Therefore, user deletes must be performed within Incorta, where the admin user will be prompted to delete the user with all content, or transfer ownership of the user's content to a different user before deleting the requested user.
In this script you will also have to update 1 line that defines how the script will log in to Incorta. Update and save this script after making the change as the below example illustrates:
- session=`$incorta_cmd login http://<IP or URL to your Incorta Analytics Application>:8080/incorta <tenant-name> <tenant admin id> <tenant admin password>`
Schedule this script to run based on your desired frequency of synchronizing users with Incorta.
Authenticating Users in Incorta using LDAP
LDAP can also be used as the method for Authenticating users in Incorta. To enable Authentication via your company's LDAP environment, you will need to update the Tenant Configuration in the CMC as follows:
- Login to the CMC console
- Navigate to the Tenant Tab, and next to the Tenant you would like to configure for LDAP Authentication, click on the link to Configure that tenant.
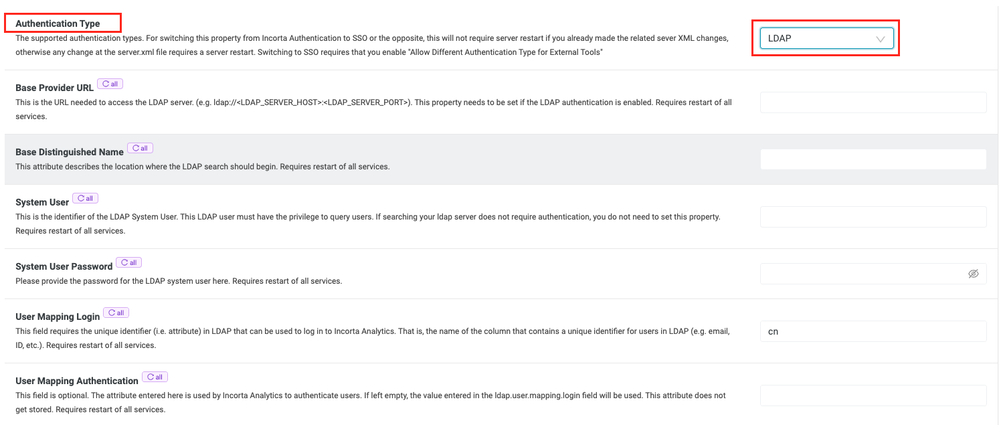
- Click on the Security Tab on the left side of the screen. The very first option on the Security page is "Authentication Type". If you clink in the Dropdown menu for this option, you will see 3 choices: Internal, SSO, and LDAP.
- If you choose LDAP, the screen will change and 6 additional configuration fields will be displayed. The first 5 are required and the last one is optional
These configuration fields match identically to the fields that must be entered in the ldap-config.properties for the following tag names:
- ldap.base.provider.url
- ldap.base.dn
- ldap.user.dn
- ldap.user.dn.password
- ldap.user.mapping.login
When using LDAP for Authentication, the user will enter his/her email or network-account and password, and if successfully authenticated, the user will be logged into Incorta. Incorta will NOT store the user's password in this case just as is the case if SSO is being used for authentication.