- Incorta Community
- Knowledge
- Administration Knowledgebase
- LDAP Sync Troubleshooting Tips
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
05-22-2022
12:38 PM
- edited on
07-05-2023
05:06 PM
by
![]() Tristan
Tristan
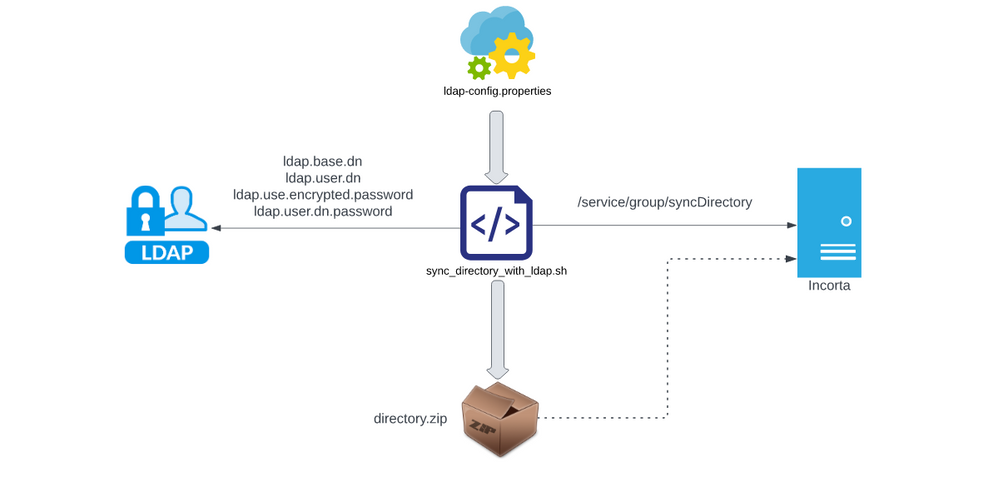
Overview for the LDAP sync process:
Common Issues
Users / Groups / Assignments are not updated in Incorta :
- Check the files within the compressed directory.zip (users.csv , groups.csv and user-groups.csv)
- Each one of those files will contain the data extracted from LDAP for the respective query
- Check for your missing user/group/assignment
- Entry does not exist in file → Check the query that gets the data from LDAP. You can test the query using 3rd party tools to make sure if the missing entry is being fetched or not. Refer to the tools part at the end of the article.
- Entries exist in the file but are not reflected in Incorta → check the log file for the ldapsync script for errors related to this entry
- Entries exist in the query output but not in the file →
- Check if the directory.zip is updated / created when you execute the script , In some cases if there is a permission issue the file can not be overwritten.
- Currently incorta doesn’t support paging in fetching from LDAP so there is a limitation on the number of users that will be fetched. The query getting the users has to be very specific in order to work within this limitation. The limit is 1000 records by default (configured from theLDAP side) in case the limit is exceeded an error (LDAP_SIZELIMIT_EXCEEDED) will be thrown.
- In case the script is scheduled with a tool like cron, make sure that the script is being triggered from the scheduler
INC_02060401: Could not connect to LDAP server with URL , INC_02060401: Could not connect to LDAP server with URL: (simple bind failed:
- Check connectivity toLDAP from the server you are executing the script on. This can be done with the below unix command. In case you can not connect (a prompt will not show), you will need to check if the port is correct or if connectivity is open between the Incorta server and the LDAP server.
- Check that you are using the correct protocol for connecting to LDAP (LDAP Vs. LDAPS) with respect to the port being used.
telnet <ldap_server_name> <port>
- Check the credentials you are using. This can be tested by 3rd party LDAP tools.
- Check if you are using the correct protocol to connect to LDAP and the port you are connecting is supporting this (ldap / ldaps)
Users are removed from ldap but not reflected in Incorta (In case that this user had been already created before):
Currently there is no way to remove users automatically because of dashboard ownership issues.
Syncing nested groups:
Below is an example of the use case:
We have a group NonProd which in turn has Developers, Bi Analyst and Admin groups. When I do the sync based on NonProd group, I'd like to see group NONProd imported to Incorta and also nested groups of Developers/ BI Analyst and Admin groups and its members.
&(objectCategory=person)(mail=*)(memberOf:1.2.840.113556.1.4.1941:=CN=group1,OU=x,DC=y,DC=z))
(&(objectClass=group)(cn=*)(memberof:1.2.840.113556.1.4.1941:=groupDn))
Users are not created with the correct type
Check the settings for the property user.type
Tools
The following 3rd party tools can be used to test connectivity, credentials and test queries for LDAP.
Test LDAP with Apache DS
Apache DS is an Open Source software that can be downloaded and installed on multiple platforms , It provides a GUI to connect to LDAP server.
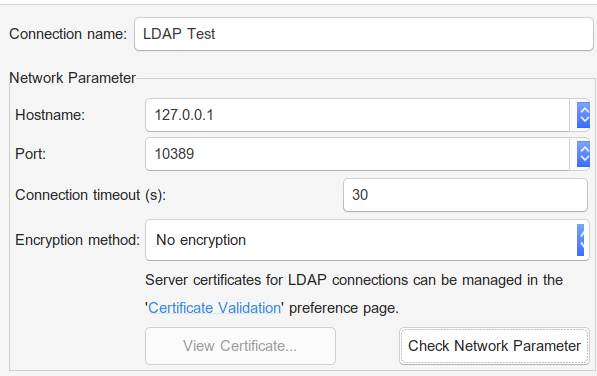
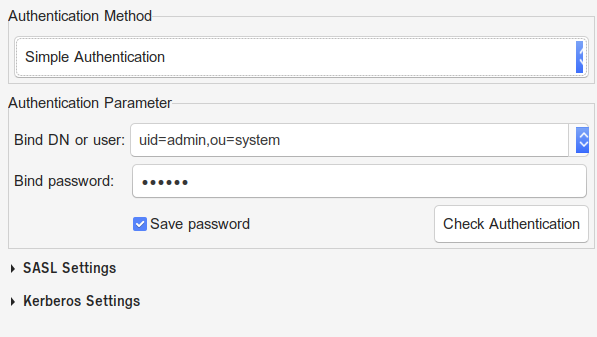
Testing LDAP with ldapsearch
ldapsearch is a command line tool that can be used to connect to LDAP and execute search queries. If the tool is not installed on your platform, it will need root access to be installed.
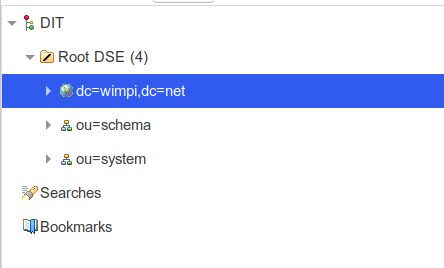
Given the below parameters:
- Base DN : dc=wimpi,dc=net
- Ldap server Host : 127.0.0.1
- Port : 10389 (non secure)
- User name : uid=admin,ou=system
Use this command:
ldapsearch -x -b "dc=wimpi,dc=net" -H ldap://127.0.0.1:10389 -D "uid=admin,ou=system" -W
The above command will output all entries in LDAP. In the PROD env this will be a lot of output so probably you will need to limit the output with search filter:
ldapsearch -x -b "dc=wimpi,dc=net" -H ldap://127.0.0.1:10389 -D "uid=admin,ou=system" -W "objectClass=person"
The above command will only output the entries with person object class.
An example for LDAP template
# Provide ldap url
# Example: ldap://HOST_NAME:PORT_NUM
# Distinguished Name to connect with
ldap.base.dn=dc=ldap,dc=test,dc=com
# Distinguished Name and password of a user in the ldap to authenticate with
ldap.user.dn=cn=admin,dc=ldap,dc=test,dc=com
ldap.user.dn.password=zyz
# The attributes that will map login name, mail and name of Incorta user
ldap.user.mapping.login=mail
ldap.user.mapping.name=cn
ldap.user.mapping.mail=mail
# The attributes that will map name and attached users of Incorta group
ldap.group.mapping.name=cn
ldap.group.mapping.member=member
# a filter to search users with given example
ldap.user.search.filter=(sn=*)
# a filter to search groups with given example
ldap.group.search.filter=(cn=*)
#user.type is optional with default (ldap) and indicates the user type, possible values are: internal, sso, and ldap
user.type=ldap
#ldap.follow.referral is optional with default (false) and indicate that it does not have a copy of a requested object and giving the client a location that is more likely to hold the object,
#which the client uses as the basis for a DNS search for a domain controller.
#Ideally, referrals always reference a domain controller that indeed holds the object.
# If set to true ,the search will be slower So Please don't use it unless you have multiple reference Site!
ldap.follow.referral=false